Anything you transmit over the Internet can be intercepted, heard, or stolen: the emails you send, the files you share, even the photos you upload.By whom? It could be anyone. It could be the government. But it could just as easily be an anonymous hacker monitoring your network like a nosy neighbor. The point is, it’s easy. And not only that, it’s cheap.
But you’re not helpless. There are tools that, when used properly, can improve the privacy of your data without forcing you to give up the conveniences of the Internet. Below are some essential tips that’ll give you all the information you need to protect yourself and increase the security of your data online.

1. A secure connection
No connection ensures privacy and total anonymity, but you can get close to it if you use a combination of anonymizers and encrypted tunnels.
The program Tor, available for many operating systems, routes your traffic through a series of nodes, making navigation anonymous. Thanks to the installation package, it’s very easy to use and configure.
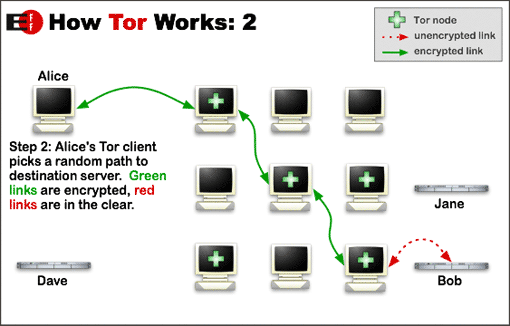
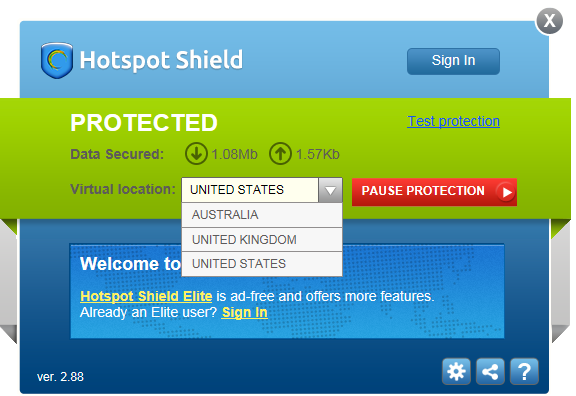
But while Tor encrypts your traffic to and within the Tor network, it doesn’t make your traffic completely soundproof. For that, you need to encrypt your connection, passing it through a tunnel, known as a Virtual Private Network or VPN. The most well known VPN clients are Hotspot Shield and Ultrasurf.
Tor can be used in conjunction with a VPN: in exchange for the loss of speed that involves using both systems, you gain anonymity and privacy, as well as the ability to open websites that may be unavailable in your country.
2. A secure browser
A web browser is where most people spend the majority of their time, and for that reason, it should be safe and offer a wide selection of security plugins. Above all, however, it should be an open source browser.
A good one is Tor Browser, a browser based on Mozilla Firefox which is pre-configured to use the Tor anonymity service. You can also use SRWare Iron, a secure version of Chrome that doesn’t send data to Google. The portable versions add a further layer of security.
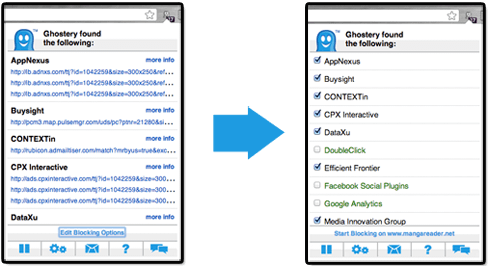
To maximize your browser’s security, you can also install extensions like Ghostery or DoNotTrackMe, which deactivate trackers. Remember that most of these programs help you stay anonymous, but don’t encrypt your traffic. For that you need to use encryption, which we’ll go into further detail about later.
3. A secure search engine
Browsing almost always begins with a search, and what you search says a lot about you. Another key to increasing privacy is, of course, a secure search engine.
Since the PRISM scandal broke, the independent search engine DuckDuckGo has emerged as one of the best secure alternatives to Google: their results are of similar quality, but DuckDuckGo doesn’t store your searches, preventing them from being associated with you.
If you want to keep using Google, a safe option is GoogleSharing, a browser extension that passes all your search requests through an anonymous server and prevents Google associating them with you.
4. Secure email
An email account contains a wealth of personal information, whether in items you’ve sent or received, which is why it’s important to protect it.
SecureGmail is an open source extension that adds encryption to your communications with Gmail (for those that use this service). To go one step further, you should use PGP or GPG, which is currently the most widely used system of encryption and secure communications. For convenience, use extensions like MailEnvelope and SecureGmail.
Still want more security? Create an account with CounterMail or HushMail, both secure mail services with integrated encryption. The alternative is to use temporary ‘disposable’ email accounts such as Guerrilla Mail or Mailinator.
5. A secure messaging app
Can’t tear yourself away from WhatsApp? You should know that it’s not a very secure app: until recently, its traffic was not encrypted and the app stored all your message history on your phone.
If the idea of using an insecure messaging app doesn’t sit well, don’t despair: there are alternatives. For mobile phones, the two most interesting are Wickr (iOS) and Gryphn (Android), which allow you to encrypt your messages using a very powerful algorithm.
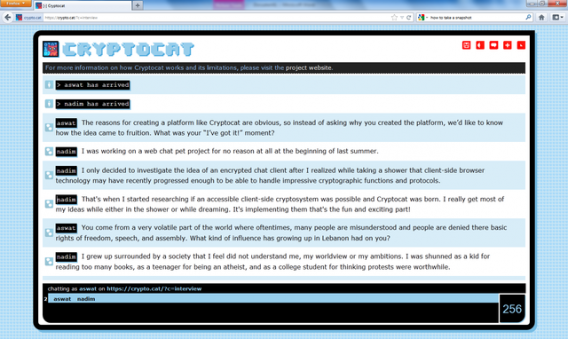
When using your PC, Cryptocat is a good option, a Firefox extension that lets you chat with strong encryption. It’s available in 32 languages and there are many journalists who use it for their confidential conversations. Used along with Tor, Cryptocat provides encryption and anonymity for your chats.
6. Secure file hosting
At some point, you might have to share large files. If you’re working with sensitive information, uploading files using certain services can be risky, especially if your servers are in countries with laws that guarantee little privacy.
A system like BitTorrent Sync, whose use is explained here, uses an ingenious system of secret keys and 256-bit encryption, making file and folder sharing both easy and safe.
With a private substitute like Dropbox, BitTorrent Sync is excellent. But there are other options too: Mega and Bitcasa use encryption to store files on their servers so that only the user knows its contents.
7. A place to copy text and images
Sometimes you might need to copy text or share photos publicly but would rather do so anonymously.
The undisputed leader for copying text is PasteBin, a kind of ‘clipboard in the cloud’ in which people share all kinds of documents and leaks with a good level of privacy. Even more secure is CryptoBin, which encrypts the text using a key.

For images, services like Imgur allow you to post images or upload files anonymously. Imgur makes it very clear: if the photo you upload is not shared publicly, it will not be seen by anyone. Make note: it’s up to you not to share the unique image links that Imgur creates if you don’t want anyone to see them.
8. An application to clean your metadata
All documents you produce contain metadata, information that may violate your privacy and expose your identity to the public.
As safe as you may think the communication channel you’re using is, the GPS coordinates on a photo or your name in a .DOC file an ruin your attempts to go unnoticed.
There are tools capable of collecting metadata from many documents in seconds, and with such programs out there, you want to make sure that your documents are clean.
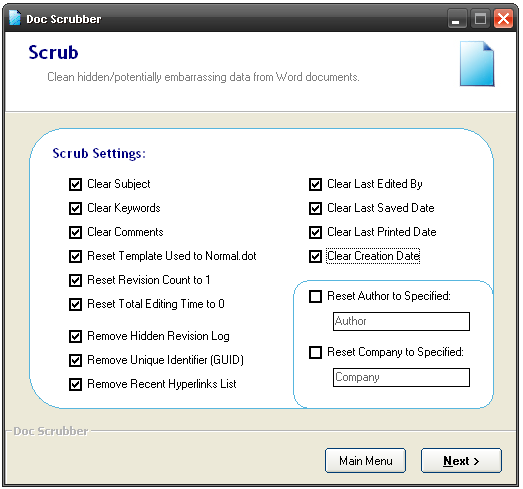
Cleaning out this information isn’t hard, you just have to know how to do it, and utilities like Doc Scrubber or MetaStripper make it very easy. In general, never share a file or a picture online without having removed its metadata.
9. A respectable online presence
Your online presence can say a lot about you, and it could be harmful if you don’t know what’s out there. Clearing your tracks is one way to stay ahead of the game.
Simplewash is an application that helps you erase your past activity on social networks. Another tool, Safe Shepherd, makes a detailed diagnosis of your online presence.
Another solution is to keep your official profiles but to create separate, or alternative, profiles for online activities that you may not want to be easily associated with you. Many people opt for this method to remain active but less visible online. Just remember to make these profiles credible and not create completely false identities.
10. A secure hard drive in your PC and the Cloud
As much as you can store in the Cloud, at the end of the day, your hard drive is still where most of your personal information is stored.
To keep your data safe from prying eyes, like a thief who has stolen your laptop or an intruder who want to tinker with your data, it’s best to encrypt your hard drive, if only partially. A program like PGP can do it, but there are free solutions just as powerful, like TrueCrypt, which encrypts virtual drives at once.
If your files are stored in Box, Dropbox and other cloud services, then you might also be interested in trying BoxCryptor, which groups together and encrypts files on your hard drive before they are synchronized to the remote server. Be careful though: as is the case of TrueCrypt, if you lose the password, you have no way to recover your files.
Cautionary note
The applications listed above can help you more effectively protect your privacy and identity online, but don’t replace them with common sense. These applications don’t always work perfectly, especially when used without previous experience, so please use discretion online.