In the middle of 2025, companies around the world have found in the cloud an efficient and scalable environment in which to optimize their operations. 98% of businesses have already implemented it into their workflow. However, this digitization of services also translates into greater exposure of their data. And hackers know it.
Only in 2024, 80% of companies admitted to experiencing some type of security breach through the cloud. One of the most notable cases was the attack by the cybercriminal group USDoD, which resulted in the theft and leakage of data affecting more than 2.9 billion people. But these are not the most alarming figures. According to a recent report by Thales, only 2% of companies encrypt 100% of their sensitive data.
In this environment of digital uncertainty, it is evident that although the cloud can be practical, it also carries hidden dangers. But… Is it possible to keep our data safe? Fortunately, yes.
To answer this question, in today’s article, we will take a tour of the current state of encryption and security in the cloud through its statistics. We will also show you how solutions like NordLocker and its encryption system with zero-knowledge policy can change our perception of the cloud.
Key Statistics on Encryption and Cloud Security (2025)
- 40% of security breaches occur in the cloud. (IBM)
- In 2024, 80% of companies experienced some incident related to the cloud. (Unit42)
- On average, 47% of the data stored in the cloud is considered sensitive. (Thales)
- 70% of organizations have sensitive and secret data unencrypted (passwords, API keys, etc.) in their cloud code repositories. (Orca)
- Less than 10% of companies encrypt 80% or more of their data in the cloud. (Thales)
The cloud security market will reach $148 trillion by 2032
Hosting IT infrastructure in the cloud has multiple advantages for businesses. Among them, greater flexibility in developing their functions stands out, as well as a considerable cost saving on maintenance.
Over the last few years, the popularity of cloud computing at the enterprise level has only increased. In fact, it is estimated that as of today, more than 90% of businesses already have some of their services digitized in the cloud.
This data drives the growth of SaaS, which can clearly be seen in its estimated price. By 2032, with a compound annual growth rate (CAGR) of 22.5%, it will reach $148 trillion.
Global cloud security market growth:
- 2022: $20.5 trillion.
- 2023: $25.1 trillion.
- 2024: $30 trillion.
- 2025: $38.6 trillion.
- 2026*: $48.4 trillion.
- 2027*: $57.9 trillion.
- 2028*: $65.9 trillion.
- 2029*: $96.5 trillion.
- 2030*: $96.5 trillion.
- 2031*: $118.2 trillion.
- 2032*: $148.3 trillion.
(Source: Edge Delta)
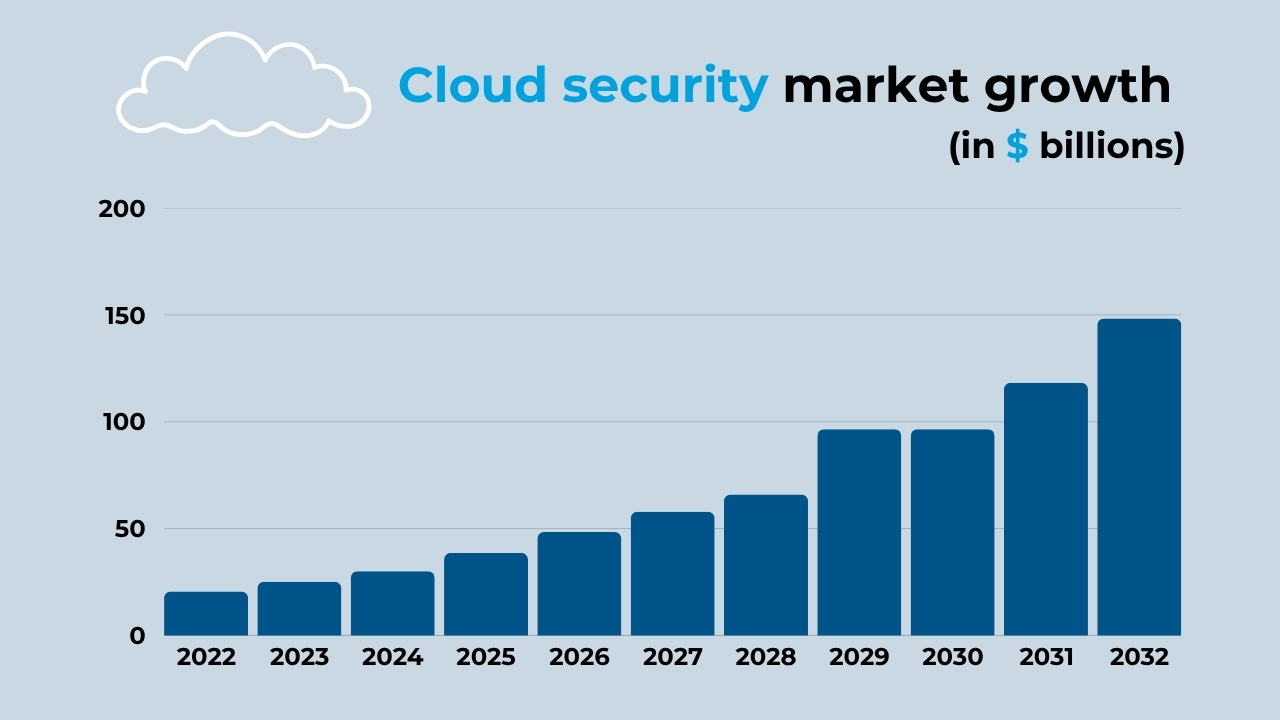
(*estimated)
2 out of 5 security breaches occur in the cloud
The majority of companies and organizations worldwide distribute their data across multiple environments, including on-premises servers as well as public clouds and private clouds. According to the recent IBM report Cost of a Data Breach 2024, 40% of security breaches and data violations occur in enterprise clouds.
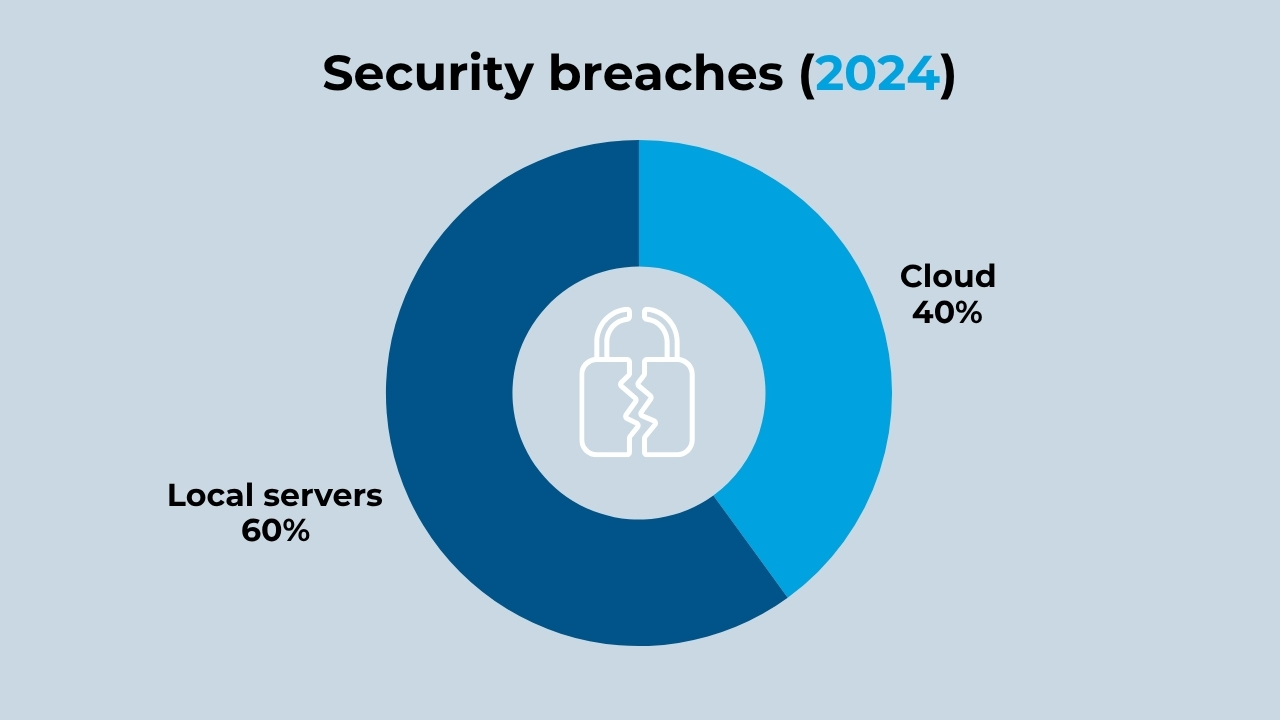
(Source: IBM)
The cloud is the main target of cyberattacks
By 2025, cloud security will become one of the primary objectives for businesses. 14% of businesses globally report having suffered a cyberattack through the cloud in the last 12 months. This data is reinforced by the fact that the cloud is at the center of hackers' sights.
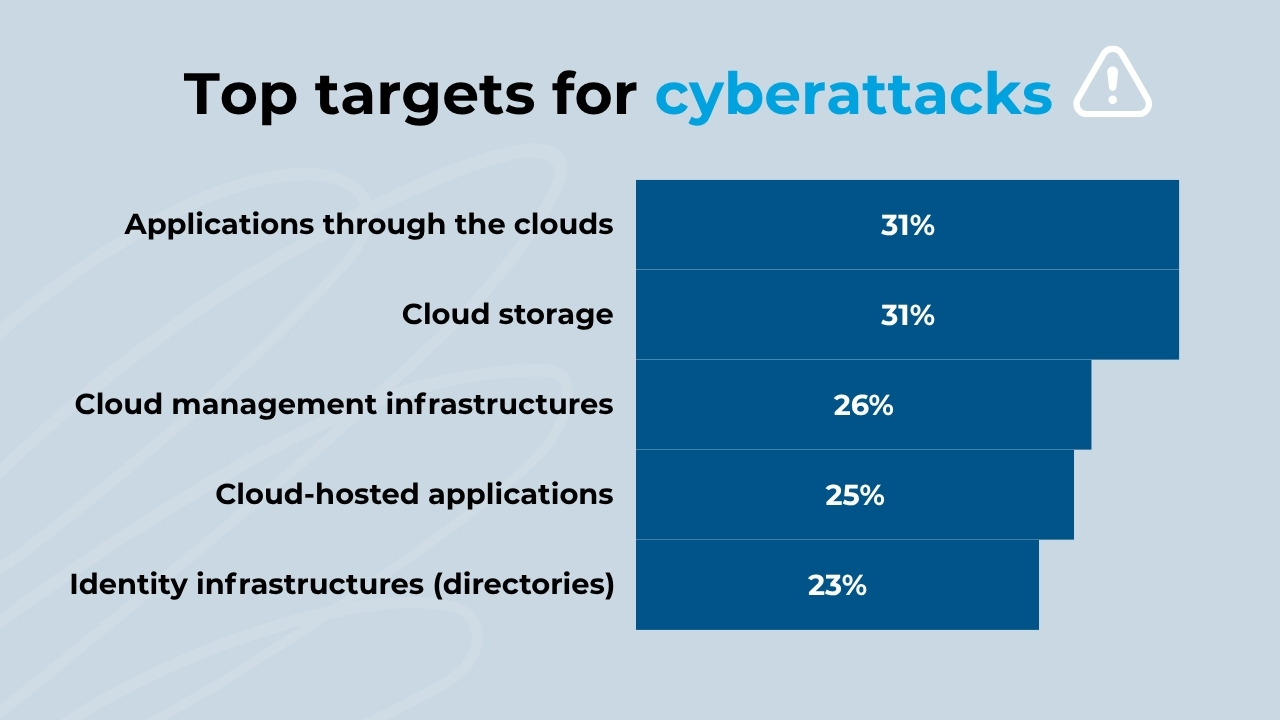
A recent study conducted by Thales shows how the cloud tops 4 of the 5 main targets of a cyberattack.
Main target of a cyberattack (2025)
- Applications through the cloud: 31%
- Cloud storage: 31%
- Cloud management infrastructures: 26%
- Cloud-hosted applications: 25%
- Identity infrastructures (directories): 23%
80% of companies have been victims of some cloud security incident
The greater adoption of the cloud by companies and corporations, as well as the exponential growth of malware and cyberattacks, go hand in hand. According to a recent study by Unit42, 80% of the vulnerabilities in a business's security were found in its cloud.
(Source: Unit 42)
Almost half of the data stored in the cloud is considered sensitive
With the cloud in the crosshairs of attackers, it is important to know what type of data is stored in these digital services. A study conducted by Thales shows us some really interesting data. Their survey of over 3000 companies in 18 countries around the world shows that, on average, 47% of the data stored in the cloud is considered sensitive.
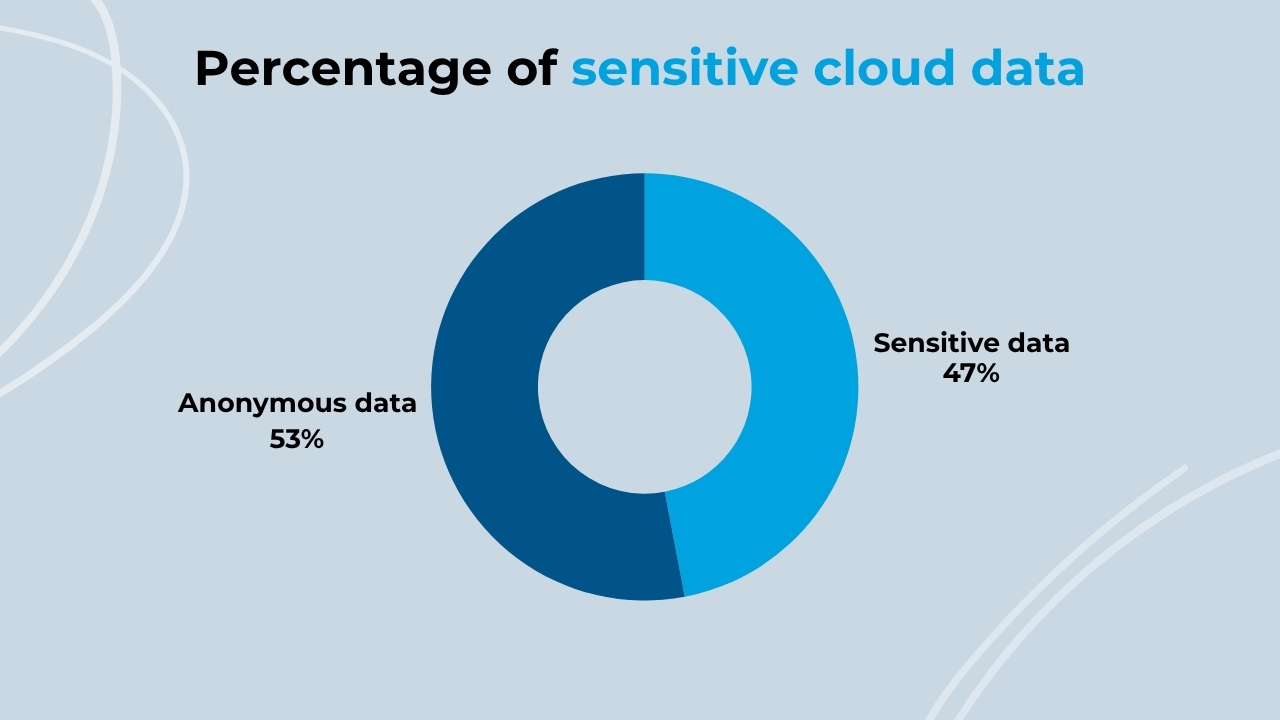
(Source: Thales )
70% of organizations have sensitive data and secrets unencrypted
Closely related to the previous point, we find this alarming data. According to the State of Cloud Security Report 2024 from Orca Security, 70% of companies have unencrypted secrets in the cloud. Among them, we find personal, financial, and banking information, passwords, and even API keys. Thus, any vulnerability could result in the theft of this data by cybercriminals.
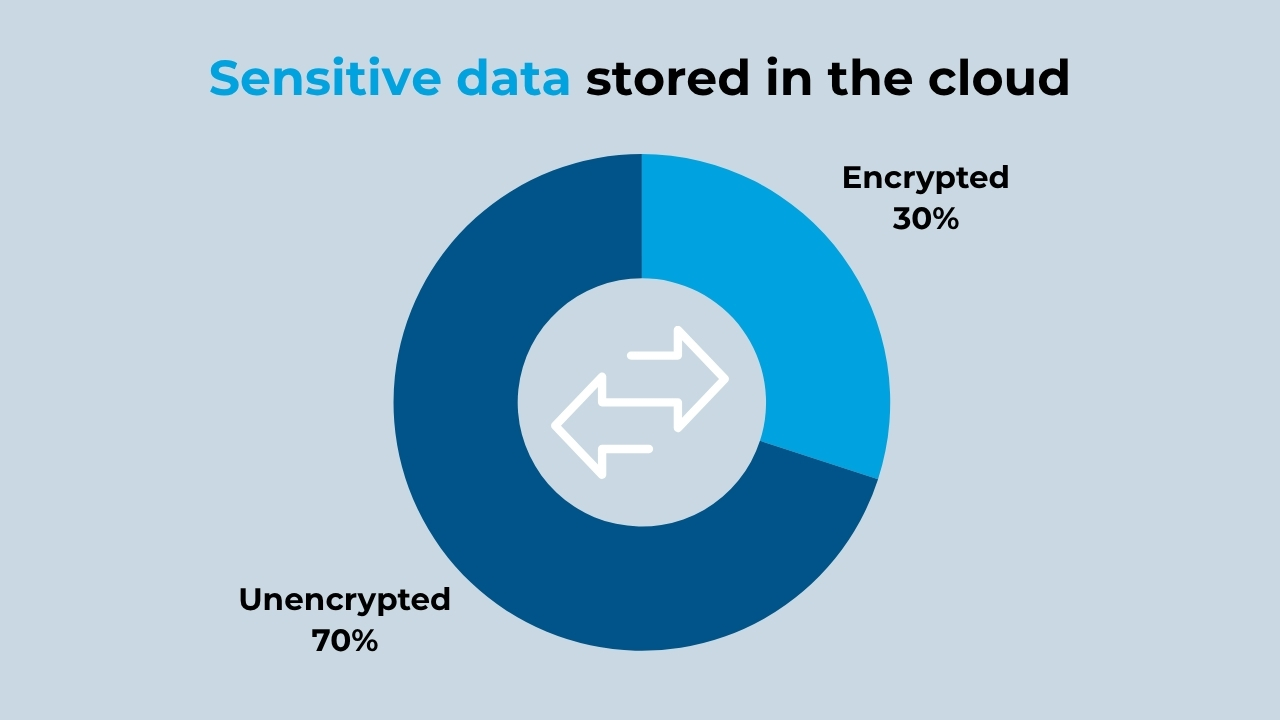
(Source: Orca Security)
Only 1 in 10 companies encrypt 80% or more of their data in the cloud.
In a landscape where cybercriminals have the cloud in their sights, the security of stored data must become a business priority. However, despite 47% of data stored in the cloud being considered sensitive, only 10% of companies claim to encrypt 80% or more of their data.
In the following table and graph, we show you the percentage of data encrypted in the cloud during the period 2021-2024.
|
0-20% |
21-40% |
41-60% |
61-80% |
81-100% |
|
|
2021 |
11% |
43% |
28% |
n/a |
n/a |
|
2022 |
11% |
39% |
27% |
12% |
11% |
|
2023 |
8% |
33% |
38% |
14% |
6% |
|
2024 |
15% |
29% |
28% |
18% |
10% |
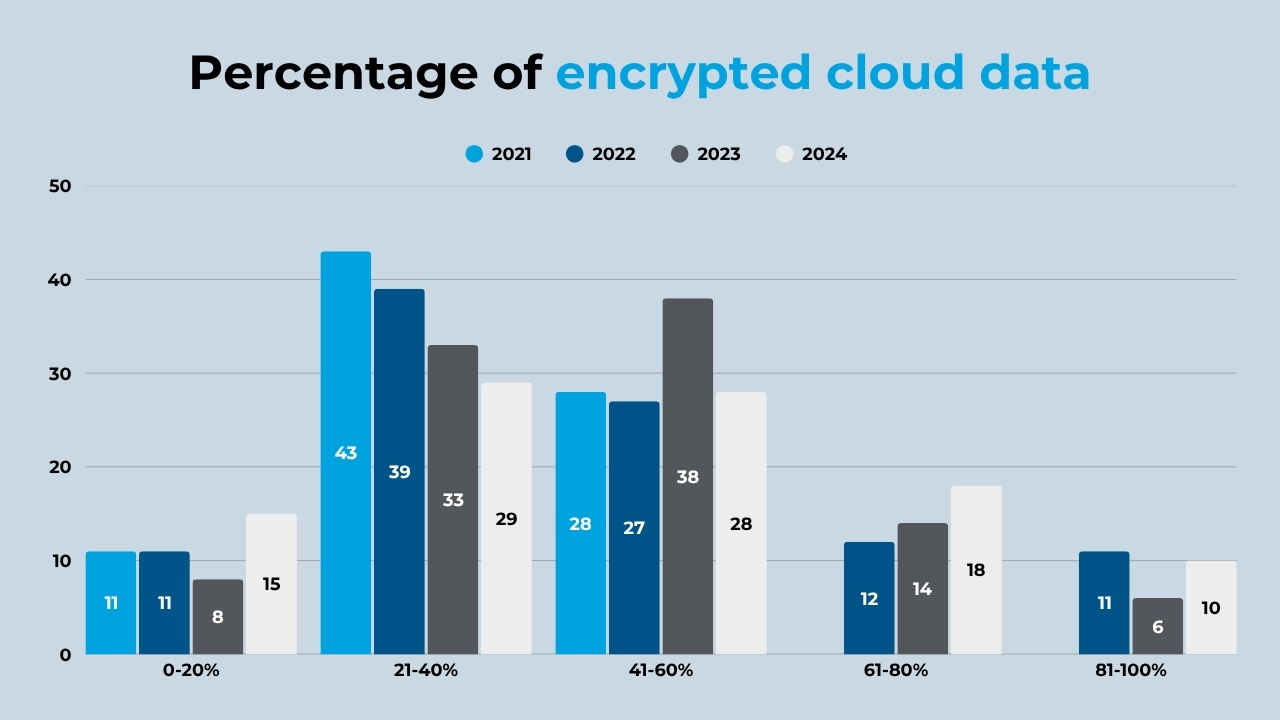
(Source: Thales)
What is NordLocker, and how can it protect your business from cloud cyberattacks?
As statistics show, the cloud offers many advantages, becoming an ally for most businesses when it comes to optimizing their operations. However, it also has its dark side. Its rapid adoption comes hand in hand with a rise in cyberattacks aimed at breaking its security. What’s the solution? Opting for a tool that keeps our online data secure and private.
NordLocker is presented as the best option on the market to ensure the privacy of your data in the cloud. Created by Nord Security, a leading cybersecurity company, NordLocker is capable of end-to-end encrypting any file you host on the Internet. This way, the cloud ceases to be just a place to store files and becomes a genuine digital safe to which only you have access.
The goal of NordLocker is simple: Eliminate any gap between security and ease of use with its innovative zero knowledge encryption (zero knowledge). This innovative security architecture is based on the fact that every file hosted by NordLocker will be encrypted even before it reaches the Internet.
But that is just one of its great advantages… What sets NordLocker apart from other solutions on the market? Next, we will explain why it is the best option for your business:
Zero Knowledge Architecture
NordLocker anticipates the statistics by shielding your business data from any cyberattack thanks to its zero-knowledge architecture. What does it consist of? Very simple. NordLocker uses end-to-end encryption where only the user possesses the encryption keys for their data.
Any stored file is encrypted before reaching the cloud, and even NordLocker is unable to decrypt your data. Thus, it is impossible for third parties to intercept or misuse any sensitive information that may be stolen.
Encryption and cloud storage
Unlike other solutions on the market, NordLocker emphasizes not only data storage but also its protection. To do this, it uses the most advanced encryption systems available: AES-256, RSA 4096 bits, Argon2 and ECC (with XChaCha20, EdDSA, and Poly1305).
NordLocker prioritizes the security of both businesses and individuals, providing different methods to safeguard their files. Thus, it not only offers the possibility of encrypting data and uploading it to NordLocker's own cloud but also of encrypting it and storing that backup copy on the users' own devices.
Secure data collaboration and sharing
One of the main advantages of cloud adoption at the corporate level is its ability to facilitate and optimize collaborative work. With the growing rise of remote work, NordLocker places special emphasis on securely sharing files through its cloud.
And it is very easy to share encrypted files between different users through this tool, without jeopardizing the security of a business. Simply share an email or a link generated by NordLocker and, if you wish, add an expiration date to your shared files for added security.
Thanks to the zero knowledge model, the data exchanged between users will be encrypted throughout the process, and only the recipients will be able to access its content.
Optimized regulatory compliance for businesses
NordLocker stands out among competitors as a tool developed not only for individuals but also for entrepreneurs and large businesses. Thus, it provides all the compliance measures necessary for those corporations that must ensure the protection of their customers' data (GDPR, HIPAA, CCPA, etc.)
Your data in the cloud is always secure with NordLocker
The cloud is, as of today, a key piece when it comes to optimizing the business processes of any company. The data speaks for itself. Its high adoption rate shows the need to move the assets of large companies to the Internet in order to improve their efficiency and productivity. However, this has also caught the attention of third parties. Indeed, hackers have found in the cloud an easy prey to deploy their cyberattacks.
With a clear paradox between the high amount of sensitive data stored in the cloud and a very low encryption rate, it is necessary to take additional cybersecurity measures. In this context, tools like NordLocker make a difference. Its focus on zero-knowledge encryption and compliance with international data protection regulations makes it a safe bet for any self-respecting business.
In 2025, protecting data in the cloud is not only fundamental to maintaining a company's reputation but also to ensuring its survival in the digital age. Are you ready to take the step with NordLocker?


