WhatsApp is one of the most used apps in the world. The app that years ago allowed us to stop relying on expensive SMS (they still exist) enjoys great popularity both in Spain and in Latin America, where Android phones are the majority. But WhatsApp also has a big problem: it is a magnet for cybercriminals.
There are more and more dangers to which we are exposed by the simple fact of using WhatsApp. From scams and frauds such as the “code sent by mistake”, to the spread of different types of malware, either simply to cause damage to the device or to steal personal data and passwords.
Recently, an investigation conducted by ESET, a cybersecurity company known for its antivirus: ESET NOD32, discovered the presence of a new malware that is affecting a multitude of people in various Latin American countries. Its purpose? To infect devices in order to steal passwords, take screenshots in apps such as WhatsApp and steal other data that would then be sent to cybercriminals.
The Trojan, known as Agent Tesla, spreads via phishing emails, in which the attackers impersonate real courier companies, even simulating the elements that make up the emails. In these, the user is told that there is a problem with a delivery and that they should download an attachment or click on a link. If we do so, the Trojan will infect our device.
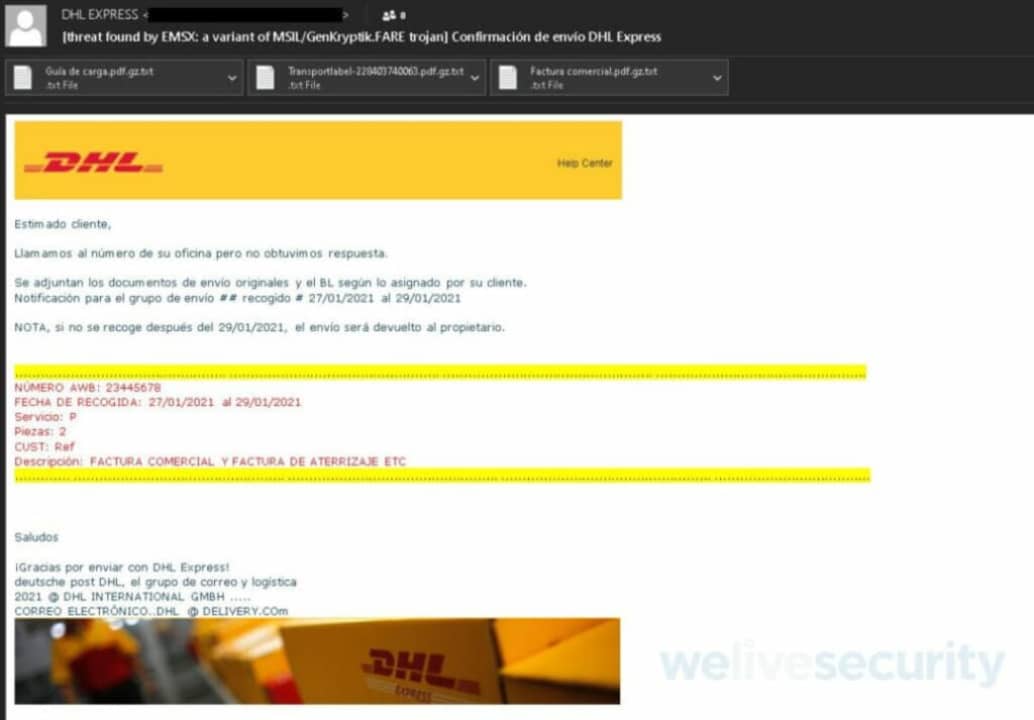
Once the Trojan is on the victim’s device, it can take screenshots of all your WhatsApp conversations (looking for passwords and personal data), save your keystrokes, steal browser passwords or even obtain information from the victim’s device.
As always in cases of scam and phishing, to prevent your device from being infected with malware you should check the sender’s address. The vast majority of malicious emails present addresses with strange domains that either do not correspond to the company they are impersonating, or are simply a series of random numbers and letters.
Some of the links added in the article are part of affiliate campaigns and may represent benefits for Softonic.


