How To
How to test the security of an Android application

- February 1, 2022
- Updated: July 2, 2025 at 3:57 AM

Before we jump right into how to test the security of your Android applications, it’s important to understand the overall nature of this popular operating system. That information will help to emphasize the importance of testing your apps before you release them into the wild.
Once you have a better understanding of how the Android OS system works, you’ll be able to perform the appropriate security testing for your device. We’ll also list some tools that can assist you.
Understanding the Android OS
Android is an open-source operating system that was launched in 2007. It’s by far the most popular mobile operating system on the planet: As of January 2022, it enjoyed around 75% market share with approximately 2.8 billion active users. It’s present on a variety of devices in addition to cell phones. It’s in your office on Chromebooks, in your home, powering your smart TV, and even accompanies you on your day-to-day in the form of wearables.
Of course, with such a huge user base, it’s a no-brainer that businesses ensure they’ve got a presence in your pocket, in your lounge, and on your wrist by having their own apps. Unfortunately, it makes Android apps a huge target for cybercriminals. If they’re able to exploit vulnerabilities in your app, there are huge commercial, reputational, and even legal risks to your organization and your users. They’re all good reasons to read on and learn more about security testing your Android applications before you launch them.
Android sandbox
By default, Android apps run in a sandbox environment. That simply means they’re unable to access any resources on a user’s device without getting explicit permission.
When a user downloads an app, it displays messages on the device’s screen requesting authorization to access things like the camera, microphone, and contacts to maximize its functionality.
Unfortunately, the sandbox isn’t guaranteed to prevent every threat. Sometimes, malicious components within an app can go undetected during the installation process, only to become active later and cause serious problems. That’s why you have to protect yourself and your end-users by carrying out penetration testing before rolling out your Android app.
Common threats
The following are four of the most common threats to the Android operating system. This is by no means an exhaustive list. It’s merely a quick look at some of the major vulnerabilities on the OS, and how to prevent them.
Binary Protection
If you allow your app to run on a rooted or jailbroken device, any kind of malicious code can run on it. At the very least, you should build jailbreak or root detection into your app.
Insufficient Transport Layer Protection
To ensure all sensitive data exchanged between the client and server is encrypted, it’s essential that your app has well-defined confidentiality and integrity rules.
Insufficient authorization/authentication
Make sure your app carries out sufficient authorization using policy-based config files instead of hard-coded checks.
Information leakage
Use threat models to ensure that data isn’t accidentally leaked through things like URL and keyboard press logging.

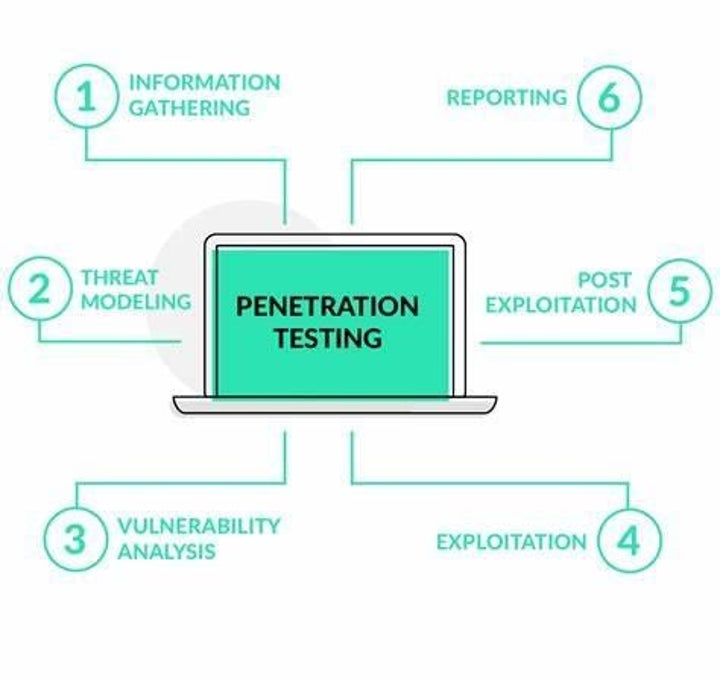
Penetration testing
Penetration testing, or pen-testing, is the process of verifying the integrity of your Android apps. It lets you identify the vulnerabilities within them and indicates the severity of each one.
Carry on reading to learn what tools you need, how to prepare, and what steps to take.
Tools
There are lots of tools you need for testing the various aspects of your Android app’s security. If you wish, you can download and run them individually (manual testing), or you can download an app that contains all you need, which will carry out all relevant tests automatically.
If you want to go down the manual route, you should look out for apps that test things like misconfigurations (e.g. QARK – Quick Android Review Kit), and MITM (man in the middle) vulnerabilities (e.g. Mitproxy).
Either way, you need programs that you can use for a variety of tests, including pen-testing, mobile testing, ROM modding, and more. To save time without sacrificing reliability, programs such as App-Use, Android Debug Bridge (ADB), and Mobile Security Framework (MobSF) contain all the tools you need.
You’ll also need an Android phone emulator (Android SDK). This is essential for simulating your Android phone on your computer screen. You use it to see how your evolving app behaves without risking your real phone and data.
If you’re security testing Android apps on behalf of a third party, you’ll also require a web application proxy (WAP). This allows you to get authentication to work with apps on a company’s private network.
Finally, You should set up a virtual machine (VM) so you can test your app for multiple platforms in one place. This will help you ensure that your app will work securely on diverse variations of the Android OS on other kinds of devices.
Preparation
Before you start testing, ensure your computer has at least 1GB of RAM (so the Virtual Machine doesn’t lag during your testing), and download the Android SDK and your testing tools of choice.
Vulnerability assessment
Once you’re ready to start the testing process, the first thing to do is check the current security state of your Android app.
This will produce a laundry list of vulnerabilities that needs to be addressed later when you put together your security strategy.
Security Testing
Running the pen-test will give you more detailed information as to the severity of each vulnerability detected in your earlier assessment.
It’s essential that you can strike the right balance in your app between server and client security, and usability. We recommend testing your app on each iteration to ensure you’ve got that balance right.
Mitigation
Your Android emulator is your best friend when it comes to resolving any vulnerabilities. Investigate and test them by activating the exploits, making yourself the ‘victim’. It’ll help you understand from a user’s perspective what happens during an active attack.
We’ve already given you some pointers about the most common threats associated with Android apps, and here we’ll summarize the three core aspects of tightening up security.
- Identification: If you overlook this vulnerability, it can allow a malicious app to present itself as an approved one. it leads to the user inadvertently allowing the malware to run on their device, believing it’s the original app they’ve approved
- Authorization: to provide full functionality, your app may require access to two other components on the user’s device. For example, an app that allows you to upload photographs will need access to the camera. During the installation process, your app should obtain explicit permission from the user to access other apps or information stored within them
- Authentication: As well as securing your app server-side, make sure you don’t leave the door open at the client end. The most secure way to secure your app client-side is by enabling biometric authentication. Depending on the hardware your app’s running on, the user can use iris-scanning or fingerprint authentication to open apps on their device and to authorize transactions and changes
Ensure the Android app is secure
The main takeaway here is that by constantly testing the security of your Android app during its development, you’re creating a secure, stress-free environment for everyone.
Ultimately, securing your app to the max produces a win-win situation. Not only do you protect your own server and systems, but you also make it as easy as possible for your users to remain secure while using your app.
You may also like
 News
NewsEven the Louvre Failed at Cybersecurity — Here’s How You Can Do Better
Read more
 News
NewsAI has been responsible for 50,000 layoffs in 2025: what can we expect in 2026?
Read more
 News
NewsValve will stop producing one of its most popular models of Steam Deck
Read more
 News
NewsA Korean thriller that promises to take over this Christmas arrives on Netflix unexpectedly
Read more
 News
NewsThis Transformers game will disappear from Steam at the end of the year, but you can buy it at a ridiculous price before that happens
Read more
 News
NewsOne of the great directors in the history of cinema has passed away
Read more