News
What Is Cybersquatting and How to Stop It with NordStellar
Cybersquatting poses a serious threat to brands, as its impact goes far beyond traffic loss—it can lead to financial damage and a loss of customer trust.
- April 14, 2025
- Updated: April 14, 2025 at 4:19 PM

Digital security is a priority. Today’s attacks come in many forms, and one of the hardest to detect, neutralize and—above all—prevent is cybersquatting. The reputation of our brands can be seriously damaged by malicious activity that seeks to exploit our online identity, and this is not something that’s easy to fix. Let’s explore what cybersquatting is, the different types that exist, the damage it can cause, and most importantly, the proactive steps we can take to avoid it.
What Is Cybersquatting and Why Should We Care?
The term cybersquatting is defined as the deliberate registration of domains related to well-known brands, and it has a significant impact on a company’s image and security. The goal is to attract traffic through user typing errors, confuse users, or even redirect them to fraudulent sites that mimic the official versions.
At a time when everything happens online, cybersquatting poses a serious threat to brands, as its impact goes far beyond traffic loss—it can lead to financial damage and a loss of customer trust.
Is cybersquatting legal? Many jurisdictions have defined this behavior as illegal and established regulations to penalize it. Legality depends on how the registered domain is used. Laws such as the Anti-Cybersquatting Consumer Protection Act do exist, but they don’t prevent the damage caused. Ultimately, it’s up to us to stop these attacks before they even happen.
Types of Cybersquatting and Practical Examples
Cybersquatting comes in different forms. The most common is typo-squatting, where attackers take advantage of common spelling mistakes in domain names. For example, someone could register “nrodstellar.com” instead of “nordstellar.com”.
Another method is name-squatting, which involves registering domains that replicate well-known names either fully or partially, with the intent of reselling them for a high price. These fraudulent domains exploit brand reputation, create ownership conflicts, and force companies into legal disputes just to recover or properly redirect their domain.
Finally, expired domain squatting happens when attackers take over domains that have expired, previously associated with well-known brands. The key here is speed—buying up domains that were forgotten or not renewed can give access to sites with existing traffic and an inherited reputation.
The Damage and Consequences of Cybersquatting
Few attacks are as potentially destructive as cybersquatting, for a simple reason: it targets the very foundation of any business—its customers. Fraudulent domains can confuse users and cause companies to lose both traffic and sales, not to mention credibility. Worse still, a fraudulent domain can also put customers at risk of fraud or phishing attempts.
Every company has a brand strategy and invests resources to strengthen it. Cybersquatting can quickly undermine those efforts. Trying to reclaim a domain associated with our brand usually involves long and costly procedures. Even though the outcome tends to favor the affected party, the economic and resource strain is something we could have avoided.
Given the potential damage, it’s clear that adopting a proactive approach to security is absolutely essential to keep these risks at bay. But how do we prevent our domains from falling victim to domain squatting?
How to Prevent Our Domains from Being Targeted by Cybersquatting
Preventing cybersquatting requires constant attention and proactive action to stay ahead of potential attacks. Beyond keeping a close eye on domain expiration dates, the best protection is to register alternative versions of our domains, including those that users might type incorrectly.
Registering these domains—at least the most important ones—not only with the main extension (.com) but also with alternatives (.net, .org, etc.) helps prevent others from taking advantage of our digital identity.
Of course, we can’t cover every possibility. That’s why automated monitoring tools to track suspicious registrations are essential to our strategy. With the right tools, we can receive real-time alerts about new registrations that resemble our brand, enabling us to respond swiftly to any impersonation attempts.
NordStellar: Know What Hackers Know with Full Threat Visibility
What Is NordStellar?
NordStellar is a threat exposure management platform developed by Nord Security, the same company behind well-known solutions like NordVPN, NordPass, NordLocker, NordLayer, and Saily eSIM.
NordStellar is designed to detect and proactively respond to cyber threats that target businesses. It helps us secure sensitive data within our organization and protect our most critical accounts through ongoing and updated monitoring.
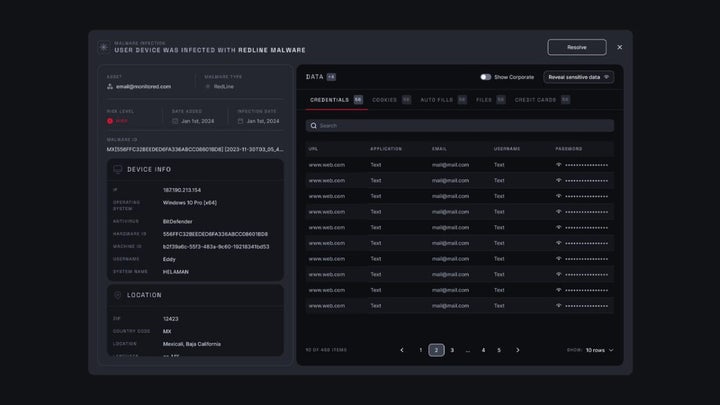
As we noted earlier in the context of cybersquatting, monitoring is essential for an early and decisive response. In the same way, early leak detection—quickly identifying exposed sensitive information—is fundamental. Beyond helping us protect our company’s trust and reputation, it helps prevent chain attacks, since catching leaked credentials in time nearly eliminates the risk of them being used for unauthorized access.
What Exactly Does NordStellar Offer?
- Leaked Data Management: Tracks potential data leaks in real time involving employees, clients, or other sensitive profiles. It lets us focus on the most critical information—such as data linked to senior executives—and gives us visibility over potentially compromised accounts.
- Data Breach Monitoring: Tracks data breaches and assesses the exposure and risk level stemming from them. The system sends automatic, immediate alerts and can even trigger response actions depending on how we’ve integrated it.
- Session Hijacking Prevention: Continuously monitors the dark web to detect stolen session cookies, compromised credentials, and signs of malware infections that may be exposing active sessions. If a threat is detected, NordStellar allows us to invalidate compromised sessions in real time, automatically blocking access attempts.
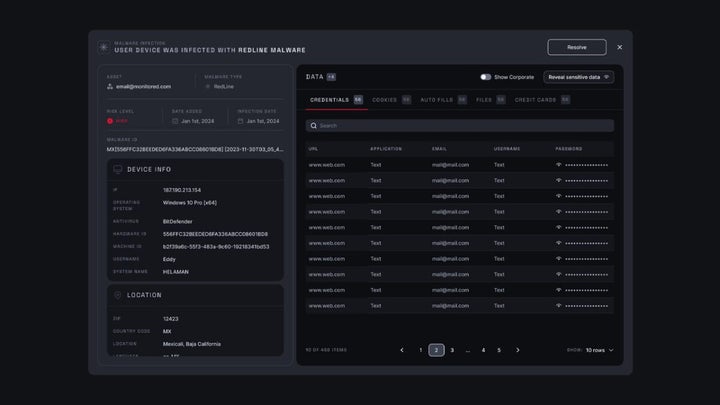
- Dark Web Monitoring: Similar to the above, this feature scans for key terms related to the company in forums, illicit markets, and hacking communities. It gives us access to the original content—messages and full posts—so we can assess severity and act quickly.
- Attack Surface Monitoring: Keeps watch over all publicly exposed points of the organization—domains, IPs, and other externally visible elements—to proactively identify vulnerabilities. It runs scheduled automatic scans and continuous monitoring for events like open ports or unauthorized changes.
Is NordStellar Easy to Use? What About Support?
NordStellar is designed to integrate easily with existing security systems, requiring minimal adjustments. The implementation process is always guided by a dedicated account manager, who helps with initial setup and customizes the system to meet our specific needs.
The online dashboard is highly intuitive and centralizes all notifications—which can also be received via Slack or email—in one place. Beyond the excellent technical support and customer service, we should highlight the specialized security consultants who are always available to guide incident response whenever needed.
As for pricing, NordStellar offers a flexible model that adapts to businesses of various sizes and requirements. And of course, we can book a live demo to see how the platform works in practice and assess its suitability for our digital environment.
How Does NordStellar Help Us Fight Cybersquatting?
Although we didn’t mention them earlier to explain them in detail here, NordStellar includes several technologies to detect, analyze, and neutralize suspicious domain registrations before they can cause damage to our brand. This is a continuous monitoring system supported by artificial intelligence, offering both visual and contextual analysis tools that are remarkably comprehensive—helping us counter any impersonation attempt.
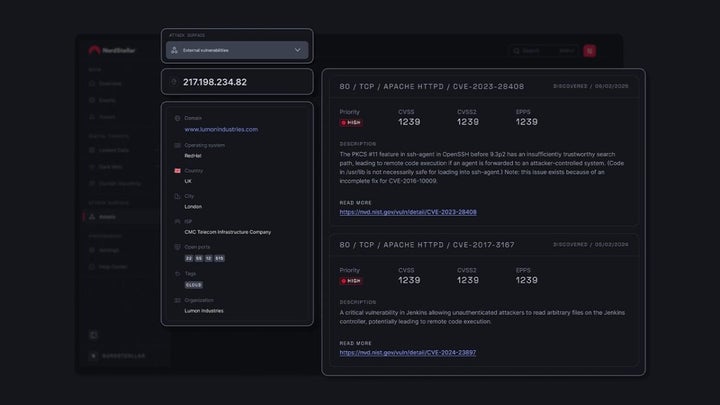
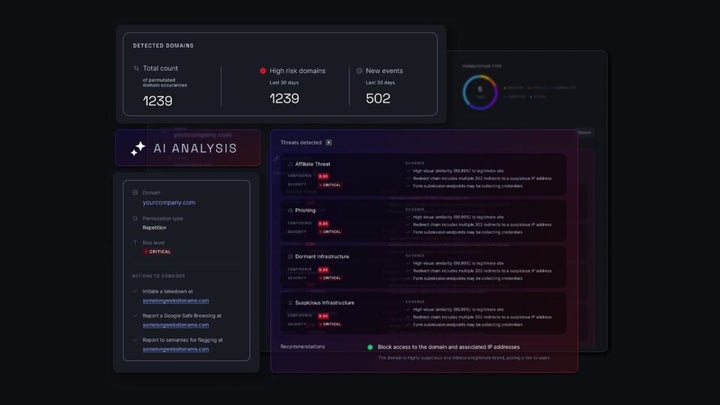
The platform constantly monitors new domain registrations and any changes to existing domains, including entries in SSL certificate transparency logs, which can be early signs of tampering. When a potentially malicious domain is detected, NordStellar compares visual elements, names, and content to our brand’s assets to immediately assess similarity. From there, AI analyzes the full context of the threat, identifies the type and severity, and provides clear evidence along with recommended actions, issuing an alert.
These alerts include screenshots of the domain, redirect chains, WHOIS data, and similarity metrics. Collecting all this manually would cost us valuable time, but here it gives us a full view of the incident, enabling fast, well-informed decisions to minimize damage before it occurs.
NordStellar introduces us to a complete threat management system—from detection to resolution. With a specialized control panel, we can track the entire lifecycle of each suspicious domain, document every action taken, and confirm its closure, acquisition, redirection or overall resolution.
NordStellar turns domain monitoring into a fully automated, efficient, and intelligence-based task, helping us protect what matters most: the reputation and trust our brand has built online.
The Power to Anticipate—or Respond Instantly When Needed
Protecting our domains from cybersquatting is as essential as it is complex. Tools like NordStellar allow us to maintain an effective defense—built on prevention, constant monitoring, and swift response to any incident—ensuring the most comprehensive protection of our digital environment.
Every preventative action and every resolved alert strengthens our brand’s image quietly but powerfully. Just as we must detect data leaks—especially involving login credentials—and understand our exposure, domain protection is another vital layer of our security. With NordStellar, we gain a strategic ally that helps us stay one step ahead of the threats, ensuring a proactive and effective defense that safeguards our reputation and our interests.
Architect | Founder of hanaringo.com | Apple Technologies Trainer | Writer at Softonic and iDoo_tech, formerly at Applesfera
Latest from David Bernal Raspall
You may also like

Disney Dreamlight Valley will reach Wonderland with its next update
Read more

Patch 8 of Baldur's Gate 3 now has a release date and this is everything you need to know
Read more

Bungie confirms that Marathon will not be a free-to-play game
Read more

This 72-year-old retiree had the best unimaginable prescription: playing Pokémon GO
Read more

A leak reveals a lot of information about the new Call of Duty
Read more

Overwatch 2 introduces its new seven versus seven game mode
Read more