How To
What is two-step verification?

- September 15, 2013
- Updated: July 2, 2025 at 8:10 AM

Passwords are a traditional, but relatively weak way of protecting your accounts. They can be easily stolen, and if they are poorly chosen, they’re really easy to guess. The same goes for physical safeguards, like keys or fingerprints – they’re easily stolen, lost, copied or obtained by coercion.
What can you do? In this case, two is better than one, and that’s exactly what lots of companies are doing with two-step verification or authentication – asking for a password and a code that you receive via your mobile phone.
Here’s a guide to what two-step verification is, how to activate it on your favorite websites, and what you need to do to make sure that it works.
What is two-step verification?
When you use your credit card to take money out of an ATM, you’re actually using two-step verification, probably without even realizing. First, you insert your card (a physical object that you possess) and then you enter a PIN code (something you know).
This is exactly what two-step verification is – using two forms of identification as opposed to only one. So, instead of just using a password, you might use a password, plus a code that you receive on your cellphone.
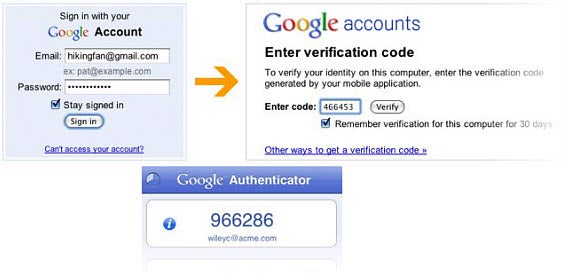
There are lots of ways to verify your identity. Just to start, you’ve got passwords, fingerprints, facial recognition, pattern creation, PIN codes, geographical location and more. This makes combining more than one pretty easy.
How does two-step verification work?
The first step is the one you’re already familiar with: entering your user name and password just like you normally would.
The new part is the second step: entering a code that you receive via your mobile phone.
Once you’ve entered the code, the PC, tablet or mobile phone that received it will be marked as a trusted device, and from then on, you’ll be able to log in with your password, without any extra codes.
What happens if I lose my phone or I haven’t got mobile coverage?
If you lose your phone, then you have a problem, since the code is sent to the number you entered on your account. Still, if you lose your phone, you can:
- Access your account via another trusted device
- Use back up codes you’ve already printed out or obtained elsewhere
If you can’t do either of these things, you can really only get a new phone with the same number or inform the website in question and follow their steps for recovering your account, a process that normally takes a few days.
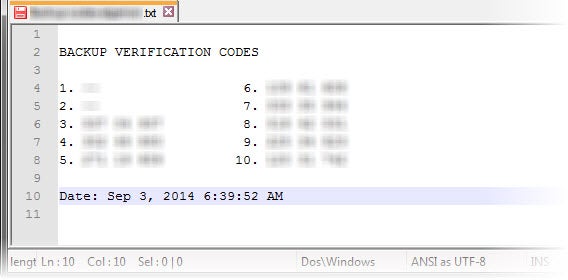
If you happen to be traveling abroad or you can’t get a mobile signal, you can use an app that produces a code offline, or use codes that you’ve already printed off.
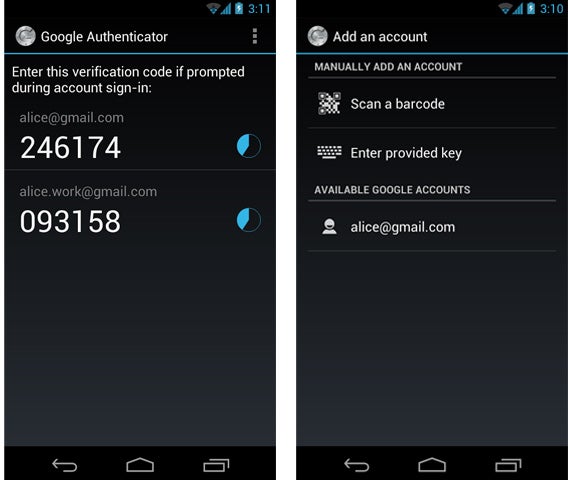
If you’re using a smartphone, I recommend Google Authenticator (Android, iOS) or Authenticator (Windows Phone), apps that produce a code even if you don’t have an internet connection. These codes are interchangeable, because they use a standard – RFC6238.
But why only two steps and not three?
Practicality. There’s nothing stopping you from using more than one verification system, but if using two is already a pain, imagine three or more.
The combined use of a password and a randomly-generated number significantly reduces the risk of unauthorized access, so it’s okay to leave the steps at two (for now).
Why have so many websites suddenly decided on two-step authentication?
It’s true, more and more websites are beginning to use two-step verification. Recent converts include Microsoft, Google, Dropbox and Twitter, to name but a few.
But why have they chosen now to make the change? Well, there are three main reasons that probably encouraged them to make the jump:
- More and more websites are choosing to centralize services under a single account (think of Google and Microsoft, for example).
- More users own multiple devices with internet access.
- There’s an increasing number of massive hacking attempts, like the one Twitter suffered back in February.
Why is two-step verification optional?
Two-step verification is largely optional because of user privacy concerns – some people don’t want their account connected to a telephone number. To get around this, some services offer physical code generators, like the Battle.net Authenticator, a keychain that generates codes when requested by the owner.
How do I activate two-step authentication?
This depends on the service. In most instances, you can log into your account, go to the account or security settings, and activate it from there. To make it easier, we’ve collected the official instructions from several websites below:
Is two-step verification infallible?
Not completely. If you’re really unlucky, a hacker could get his or her hands on your phone and also somehow know your password. Alternatively, someone who knows your password could have access to a device that has already been marked as trusted.
Trojans and phishing are two more dangers. If a hacker manages to convince you that they are a legitimate entity or, via some other means, intercepts your data, you’re totally exposed. Some Trojan viruses even manage to coordinate their actions, with a PC virus modifying what you do online, and another one on your phone intercepting the codes.
To minimize these risks, you need to add extra layers of security to your devices, like decent anti-viruses and good device passwords. Although two-step verification is very effective when it comes to minimizing the risk of intrusion, the bad guys aren’t stupid, and will look for other ways to get their hands on your information. Remember to always stay alert, and be on the look-out for anything strange or suspicious.
Follow me on Twitter @remoquete
Related Articles:
Why it’s time to start using a password manager
FBI & CIA use the same software as hackers to access iCloud accounts
Which password manager should you use – 1Password, Dashlane, or LastPass?
Original article published on April 24th 2013.
You may also like
 News
NewsThe White House warned Apple, Nvidia, and AMD that Taiwan could be invaded by China in 2027
Read more
 News
NewsThere is only one sport that has true drama: Formula 1, and Netflix shows you that
Read more
 News
NewsThe alliance between Netflix and Warner is in danger: Paramount has a better offer
Read more
 News
NewsNew trailer of the fake reality show that has left half the world speechless
Read more
 News
NewsThe protagonist of 'Community' has a series you didn't know about… And it has just been renewed for a season 5
Read more
 News
NewsYou can now play for free on Steam the demo of this game visually like few you've seen
Read more