Article
Don’t Believe the Most Popular Myths about Private Data Security
Kromtech Security Research Center
- September 5, 2017
- Updated: March 7, 2024 at 6:04 PM
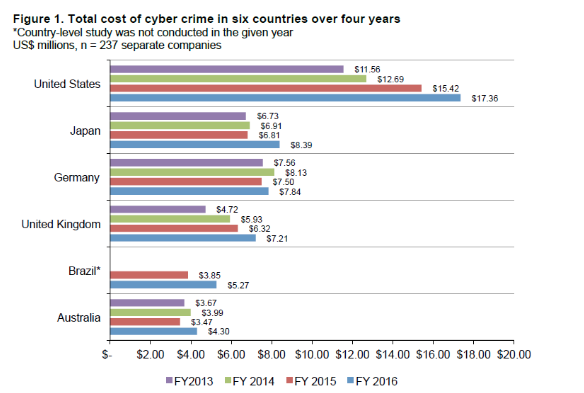
Reading articles about cyber crimes, people often think this is something that only happens in Silicon Valley or among huge IT corporations. In fact, cyber crimes may affect the lives of every Internet user. Most users don’t even understand how their private data can be exposed without their permission and knowledge even though the level of invisible cyber attacks increases every day. According to the latest statistics, the estimated annual cost of cyber crime committed worldwide adds up to 100 billion dollars! Besides companies and banks, this amount also includes individual users.
Every day many people jauntily connect to the Internet thinking they are totally secure. How then, do cyber criminals go on to earn huge amounts of money?
We are going to eliminate the 3 main myths about users’ private data security and show you the best way to stay protected whilst surfing the Internet.
1. Social Media provides you with a trusted circle of online friends
As the statistics show, the number of internet users using social media services online is up to 64%. That’s why they are the first to be targeted by cyber attacker. These are the most popular types of internet fraud:
Like-jacking and link-jacking: When you click the “like” button or follow the fake link posted by a hidden criminal, you are redirected to malware infected websites that may affect your system by installing malware or spyware.
Phishing: Attempts to obtain sensitive information such as usernames, passwords, and credit card details, often for malicious reasons, by masquerading as a trustworthy site in an electronic communication.
Social spam: Unwanted spam content appearing on social networks or any websites that have user-generated content like comments, chat, etc. and can include personally identifiable information

According to Statista* as a result of the above more than 600.000 Facebook accounts are compromised every single day!
2. Out-of-date system is not vulnerable
The point here is that software like Java or Adobe is often out-of-date and can be extremely vulnerable. They’re then vulnerable to being hit by exploit kits (software kit designed to run on web servers, with the purpose of identifying software vulnerabilities in client machines communicating with it, and discovering and exploiting vulnerabilities to upload and execute malicious code on the client).
This has become popular because Java and Adobe Flash are installed on almost every computer. All a hacker needs, to get a full access to your computer is a single click on an infected advertising banner.

To avoid this type cyber attack you should keep your software updated all the time; keep your operating system up to date; have a reliable AV installed on your computer.
3. Deleted files cannot be recovered and used without your permission
Do you know that when you “delete” files from your computer, they can remain on your hard disk? Actually, every deleted file can be recovered. In many cases, deleted files can be recovered with little effort because most computer operating systems will only delete links to the data so you can no longer see them, but the actual data remains on the disk.
Getting access to the deleted data is as simple as restoring the links. Whether it’s sensitive financial data, business documents, or scandalous photos that could be used for blackmailing you probably don’t want people getting their hands on your private stuff.
Fortunately, there are some steps you can take to protect your data by deleting files for good. Use Secure Empty Trash on a Mac. Files deleted this way are completely overwritten by meaningless data. Just drag the items into the Trash, then choose Finder > Secure Empty Trash. Unfortunately this option is no longer available for mac OS X 10.10 and later. However, you can do this another way if you install special software.
Now that you know the main delusions concerning surfing the Internet safely you should follow our advice so that you can feel more confident getting involved in social networks or dealing with sensitive and private information. Always remember, you are the one who is ultimately responsible for your online security. Fortunately, there are many programs that can significantly simplify a user’s digital life.
You may also like

Experience Supercar Speed: ZEEKR’s 7GT Accelerates from 0-100 km/h in Just 2.95 Seconds
Read more

Rising Tensions: Protests and Counter-Protests Highlight Political Divide in America
Read more

Is this the end of HDMI? These ports could replace it
Read more

New Battery Plant Promises Over 1,100 Jobs in US
Read more

If you have to pay for only one AI subscription, this is the best one
Read more
ChatGPT is the most downloaded app in the world, but is it enough?
Read more